New Cybersecurity Technology: Top 10 Tools to Protect Data
Discover the best cybersecurity tools of 2025 to protect business data. Learn how data discovery, backup, firewalls, antivirus, and compliance with GDPR, PCI, SOX, and CCPA keep your company safe.

For any business, big or small, keeping sensitive data safe is very important. Sometimes, it's the law. The type of new cybersecurity technology you need depends on the kind of data you have. You might need to follow rules like PCI, SOX, GDPR, or CCPA.
There are many ways to protect sensitive data by following these rules. Because of all the data breaches, it’s smart for businesses to use more than one security solution to be extra safe.
Real-World Examples of Cybersecurity Breaches

To understand the importance of data protection, let’s look at some real-world breaches:
-
Target Data Breach (2013): Hackers accessed credit and debit card information of over 40 million customers due to a third-party vulnerability.
-
Equifax Breach (2017): A failure to patch a known vulnerability led to the exposure of sensitive data for 147 million individuals.
-
Facebook Data Leak (2019): An unprotected database exposed over 540 million user records to the public.
These examples highlight the consequences of inadequate security measures, including financial losses, legal repercussions, and damaged reputations.
Legal Implications of Data Breaches

Failing to protect sensitive data can result in hefty fines and legal actions. Regulations like GDPR can impose fines up to €20 million or 4% of annual global turnover—whichever is higher. U.S. laws like CCPA can lead to penalties up to $7,500 per violation. Businesses must ensure compliance with these regulations to avoid such consequences.
Tips for Choosing the Right Tools

When selecting cybersecurity tools, consider the following:
-
Business Size: Small businesses may prioritize affordable solutions, while large enterprises need scalable tools.
-
Data Sensitivity: Tools should align with the type and volume of data your business handles.
-
Integration: Ensure the tools integrate seamlessly with existing systems.
-
Vendor Reputation: Choose reputable vendors with proven track records.
TOP 10 New Tools for Protecting Data
Data Discovery and Classification Software
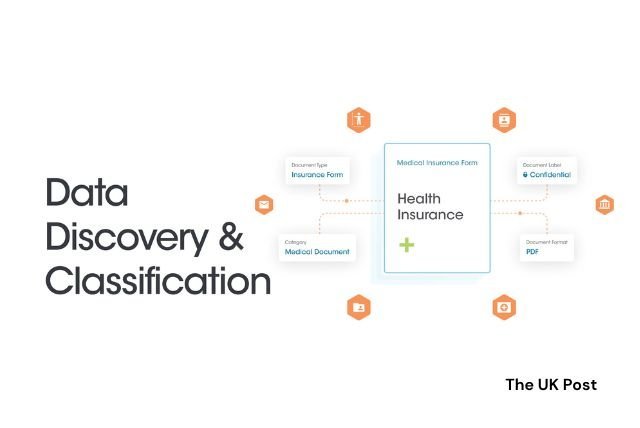
A big part of keeping data safe is knowing what’s important and where it is. A special tool can check all your data and sort it based on privacy rules like PCI DSS, IP, and GDPR.
This tool gives each type of data a special code to show how sensitive it is. This way, you can add more security where it’s needed most. Using this tool with others helps your team find out where sensitive data is, how it’s protected, and where it’s going.
Backup and Recovery Systems
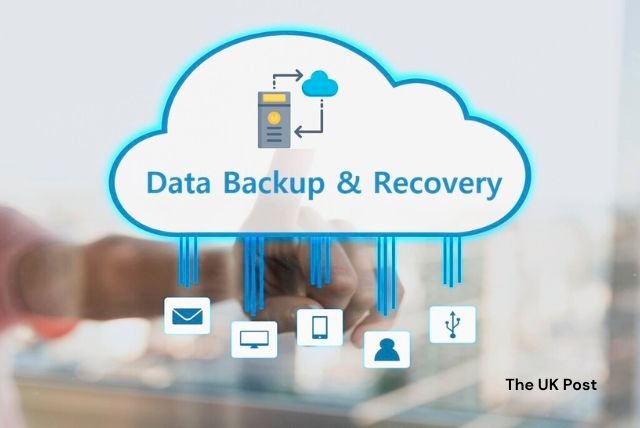
Backup and recovery systems are very important for keeping data safe. They make copies of data to protect it from getting lost due to cyber attacks, mistakes, broken hardware, or natural events. Good backup and recovery systems help organizations quickly get their data back and keep working, reducing downtime and data loss. These systems should be part of the organization's plans for handling disasters and incidents, making them stronger against cyber problems.
Firewall

A firewall is like a guard for your computer or network. It blocks bad stuff like viruses from getting in. It also keeps some parts of your computer closed to the outside world to stop hackers. Having both software (a program) and hardware (a device) firewalls is a good idea, especially to protect important data. Most computers have a basic firewall, but businesses might need stronger ones for extra safety.
Antivirus and Anti-malware Software
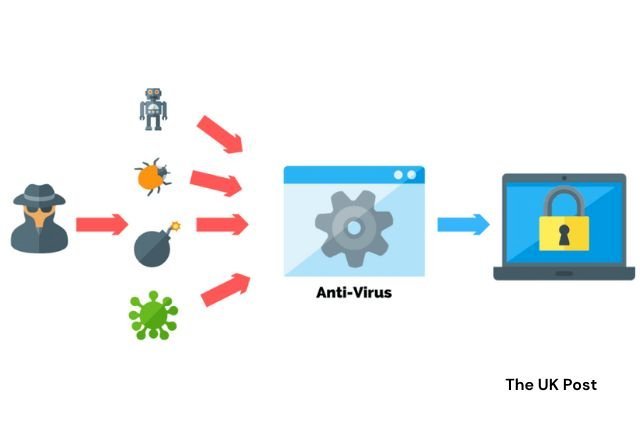
Antivirus and anti-malware software protect your computer. They are like security guards. They keep bad things like viruses and malware out of your computer. These programs can find and remove harmful stuff like trojans, viruses, and rootkits. These bad things try to damage or steal your data. Antivirus and anti-malware software stop them.
Data Loss Prevention (DLP)
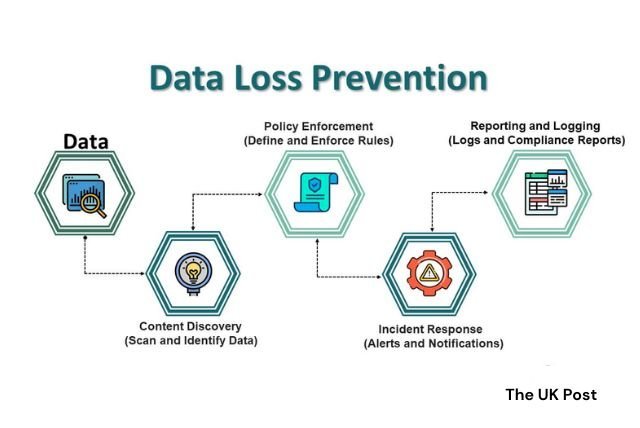
Data loss prevention tools keep an eye on your computer systems. They make sure important information isn't taken, changed, copied, or moved without permission. They can also track who is doing what, so you know if something suspicious happens.
These tools help your business follow security rules. They check for problems, report anything unusual, and tell administrators about weak spots that need fixing.
Employee Monitoring Software
Employee monitoring software watches what workers do on their computers. It checks if they are working well and looks for any problems. It tells bosses if something is wrong, like if employees go to places they shouldn't, do strange things at work, log in at odd times, or track every key they press. It's also good for watching people who work from home.
Security Information and Event Management (SIEM)
User and Entity Behavior Analytics (UEBA)

User and Entity Behavior Analytics (UEBA) watches what people do on computers. It learns what is normal for each person and notices anything strange. If someone does something unusual, like looking at odd files, it tells the boss. This helps keep the computer safe. When used with other security tools, UEBA can also find out if someone inside the company is doing something bad or if their computer is hacked.
Intrusion Detection and Prevention Systems (IDS/IPS)
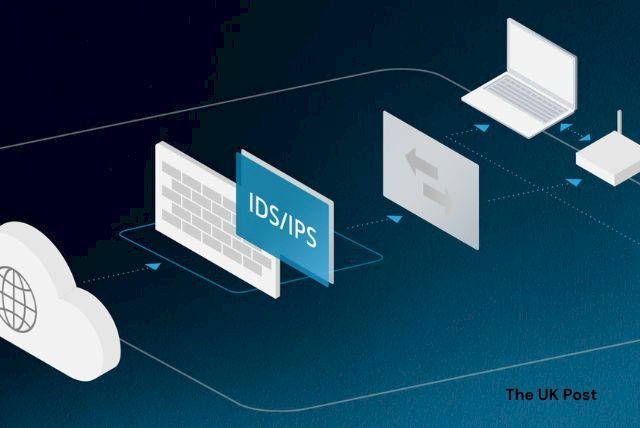
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) act like guards for your network. They watch the traffic and note anything unusual. The person in charge can adjust the settings. If they find something strange, it's checked before taking action. Data Loss Prevention (DLP) software adds another layer of safety, stopping hackers from stealing your files.
Network Security Solutions

Besides antivirus and firewall, businesses should look at other ways to keep data safe. They should control who can access the network, secure data in the cloud, and check everything regularly for weaknesses.
They need to do regular checks and tests to find any security gaps. Using tools like encryption, which makes data unreadable to unauthorized people, and making sure only trusted people can get into the system is also important.
Protecting sensitive data should be a top priority for any business. If you're worried, think about getting extra help from experts and using services that follow strict data protection rules like PCI SSD and GDPR.
Read Also: 10 Digital Strategies for B2B Marketing for Technology Companies
Emerging Threats and How to Counter Them

Cybersecurity is an evolving field. Here are some emerging threats and ways to address them:
-
AI-Powered Phishing: Train employees to recognize phishing attempts and use email security tools.
-
Ransomware-as-a-Service (RaaS): Invest in robust backup systems to recover encrypted data without paying a ransom.
-
Deepfakes: Use AI-driven detection tools to verify content authenticity.
Integration of Cybersecurity with Business Processes

Cybersecurity should not be confined to the IT department. Here’s how it integrates with other processes:
-
HR: Secure employee records with encryption and access control.
-
Finance: Use fraud detection tools to prevent unauthorized transactions.
-
Operations: Ensure supply chain security by vetting third-party vendors.
Cybersecurity for Remote Work

Remote work introduces unique challenges. To address them:
-
Use VPNs to secure connections.
-
Implement multi-factor authentication (MFA) for remote access.
-
Train employees on secure practices, like recognizing phishing emails and safeguarding devices.
Step-by-Step Guide to Creating a Data Protection Strategy
-
Assess Risks: Identify potential threats and vulnerabilities.
-
Classify Data: Use tools to categorize data by sensitivity.
-
Implement Tools: Deploy appropriate cybersecurity solutions.
-
Train Employees: Conduct regular training sessions on security best practices.
-
Monitor and Update: Continuously monitor systems and update tools as threats evolve.
Checklist for Data Protection

-
Install firewalls and antivirus software.
-
Use data classification tools.
-
Regularly back up data.
-
Monitor employee activities.
-
Conduct regular vulnerability scans.
-
Train employees on security protocols.
-
Ensure compliance with data protection laws.
Conclusion
keeping your data safe is very important for all businesses, big or small. With new cybersecurity tools, you can protect your data from cyber attacks and data breaches. Use different tools like special software to find and organize important data, systems to back up files, firewalls to block harmful stuff, and antivirus software to stop viruses. Also, keep an eye on what employees do on their computers and watch for anything strange. By using these tools and following security rules, businesses can keep their data safe and stay legal.
FAQs
Why do businesses need to keep data safe?
Businesses must protect data to follow laws, keep customers' trust, and avoid problems like data breaches that can harm their reputation and money.
What kinds of data do businesses need to protect?
Examples include personal details of customers (like names and payment info), employee records, company secrets, financial data, and anything else that could cause trouble if it falls into the wrong hands.
What tools help businesses keep data safe?
Tools like sorting software, backup systems, firewalls, antivirus programs, and monitoring software are used to protect data.
How can businesses make sure they're doing a good job at protecting data?
By regularly updating security methods, teaching staff about risks, controlling who can access data, checking security often, and staying informed about new threats.
What should businesses do if data gets stolen?
Act fast to stop more data from getting out, check how bad the damage is, tell affected people and authorities, fix things so it doesn't happen again, and help those affected while working to rebuild trust.




























