Types of Keys in DBMS: Understanding Their Importance and Functions
Discover the different types of keys in DBMS and their roles in database management. Learn about primary keys, foreign keys, composite keys, and more.

In the world of databases, keys are crucial elements that help in organizing, managing, and retrieving data efficiently. Understanding the various types of keys in a Database Management System (DBMS) can greatly enhance one's ability to work with databases effectively. These keys serve as identifiers and play a central role in establishing relationships between different tables, ensuring data integrity, and enabling efficient query processing. This article explores the different types of keys in DBMS, shedding light on their unique characteristics, functions, and why they’re essential for any well-structured database.
1. Primary Key

A Primary Key is a unique identifier for each record in a database table. It ensures that each entry in a table is distinct, which is essential for identifying individual records. Primary keys play a critical role in maintaining data integrity by preventing duplicate entries.
- Key Characteristics:
- Must be unique for each record.
- Cannot contain NULL values.
- Each table can have only one primary key.
- Example: In a table storing student records, the “StudentID” could be a primary key, as each student will have a unique ID.
Primary keys are fundamental to relational databases, as they help establish relationships between tables by serving as references in other tables.
2. Foreign Key

A Foreign Key is a field in one table that uniquely identifies a row in another table. It establishes a relationship between two tables, creating a link that ensures referential integrity.
-
Key Characteristics:
- Links records between two tables.
- Helps maintain consistency by ensuring that the referenced data exists in the related table.
- Can contain duplicate values and NULLs.
-
Example: In a database with "Students" and "Courses" tables, the "StudentID" in the "Courses" table can be a foreign key that references the "StudentID" in the "Students" table.
Foreign keys are instrumental in linking related data across tables, making complex queries and data retrieval more streamlined and accurate.
3. Candidate Key

A Candidate Key is any column or combination of columns that can uniquely identify a record in a table. Unlike a primary key, there can be multiple candidate keys in a table.
-
Key Characteristics:
- Uniquely identifies records in a table.
- Can act as an alternative to the primary key.
- Must contain unique values without NULLs.
-
Example: In a table of employee records, both “EmployeeID” and “Email” can be candidate keys, as they both uniquely identify each employee.
Candidate keys provide flexibility in database design, allowing for alternate options for identifying records uniquely.
4. Composite Key

A Composite Key is formed by combining two or more columns to create a unique identifier for a record. This key is used when a single field isn’t sufficient to ensure uniqueness.
-
Key Characteristics:
- Comprises two or more columns.
- Uniquely identifies records through a combination of fields.
- Each component of the composite key must be unique only in combination.
-
Example: In a table recording class enrollments, “StudentID” and “CourseID” together could act as a composite key, as one student can enroll in multiple courses, but each combination is unique.
Composite keys are helpful when dealing with complex data where no single field is unique by itself.
5. Super Key

A Super Key is a set of one or more columns (including candidate and primary keys) that can uniquely identify rows in a table. A super key may contain additional attributes beyond what is necessary to uniquely identify records.
-
Key Characteristics:
- Can contain extra attributes beyond those needed for uniqueness.
- Any field or combination of fields that includes the primary key can be a super key.
-
Example: In an employee table, both “EmployeeID” and “(EmployeeID, DepartmentID)” are super keys, as they can uniquely identify each employee.
Super keys provide flexibility, allowing for different combinations that can serve to uniquely identify records, although some may contain redundant information.
6. Alternate Key
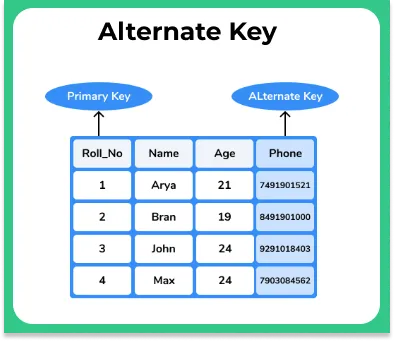
An Alternate Key is a candidate key that is not chosen as the primary key. It serves as an alternative unique identifier for records within a table.
-
Key Characteristics:
- Unique but not designated as the primary key.
- Acts as a backup identifier if the primary key is not used.
-
Example: If “EmployeeID” is the primary key in an employee table, an alternate key could be “Email” if it also uniquely identifies each employee.
Alternate keys add flexibility, providing other means of unique identification without conflicting with the primary key.
Read Also: Exploring Different Types of Wireless Data Transfer Technologies
7. Unique Key

A Unique Key ensures that all values in a column are unique, much like a primary key. However, unlike a primary key, unique keys can accept a single NULL value.
-
Key Characteristics:
- Maintains uniqueness across rows in a table.
- Allows one NULL value.
- Multiple unique keys can be created in a single table.
-
Example: In a “Users” table, the “Username” could be a unique key as each user has a unique username, although some fields may remain unassigned initially.
Unique keys help enforce data integrity by preventing duplicate values in specific columns without strictly enforcing non-null requirements.
8. Surrogate Key

A Surrogate Key is an artificially created key that has no intrinsic meaning outside of uniquely identifying each row in a table. These keys are often system-generated and are usually numeric or alphanumeric.
-
Key Characteristics:
- Has no real-world meaning and is purely for database use.
- Commonly system-generated, such as using auto-increment fields.
- Used when no natural key exists or to improve performance.
-
Example: An auto-incremented “OrderID” in an order table can act as a surrogate key, providing a unique identifier without representing real-world data.
Surrogate keys simplify database management, especially in cases where natural keys are complex or unwieldy.
9. Additional Specialized Keys

While the above keys are the primary types in DBMS, there are a few additional specialized keys used in more complex database scenarios. These include:
- Natural Key: A key derived from real-world data that is meaningful outside the database, such as a Social Security Number.
- Artificial Key: Similar to a surrogate key but manually created rather than system-generated.
- Compound Key: A composite key formed by combining two or more columns.
- Secondary Key: Used for indexing or searching, providing faster query responses.
- Recursive (Self-Referencing) Key: Used in hierarchical data, where a record references another record within the same table.
These specialized keys are less commonly used but play important roles in specific database structures or advanced data management, enhancing retrieval efficiency and database flexibility.
Conclusion
Understanding the various types of keys in a DBMS is essential for anyone working with databases. Each key type serves a unique purpose, whether it’s maintaining data integrity, establishing relationships, or ensuring efficient data retrieval. Primary keys and foreign keys are central to relational databases, linking tables and ensuring data consistency. Other keys, like candidate, composite, and surrogate keys, offer flexibility and additional options for structuring data effectively. By using these keys appropriately, database professionals can design robust, efficient databases that are easier to manage and scale.
FAQ
-
What is the purpose of a primary key in DBMS?
The primary key uniquely identifies each record in a table, ensuring no duplicate entries and maintaining data integrity. -
How is a foreign key different from a primary key?
While a primary key uniquely identifies records within its own table, a foreign key references the primary key in another table to establish relationships. -
Can a table have more than one candidate key?
Yes, a table can have multiple candidate keys, which are potential unique identifiers, though only one will be chosen as the primary key. -
What is a composite key?
A composite key is a unique identifier made by combining two or more columns, especially when no single field uniquely identifies records. -
Why are surrogate keys used in databases?
Surrogate keys are artificial identifiers without real-world meaning, often used to simplify database management or when natural keys are too complex.

















